Agentic security for agentic AI
Secure every AI agent you build or buy with continuous red teaming and real-time guardrails.
When Agentic Apps Emerge, Threats Follow
What once took months to build now takes a single prompt — speak it into existence and an app appears that can reason and act. But speed brings risk: over-permissioned agents, hidden prompts, and unpredictable behaviors. Creation is easy. Control is not.
AI Agents: Autonomous Power & Chaos
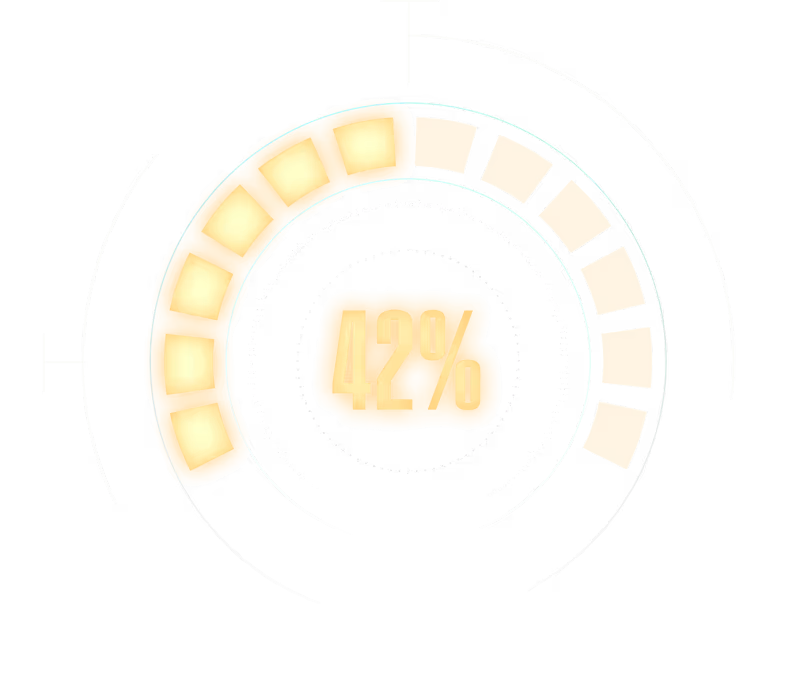
42% of companies have deployed agents. That is a 11% more than two quarters ago.
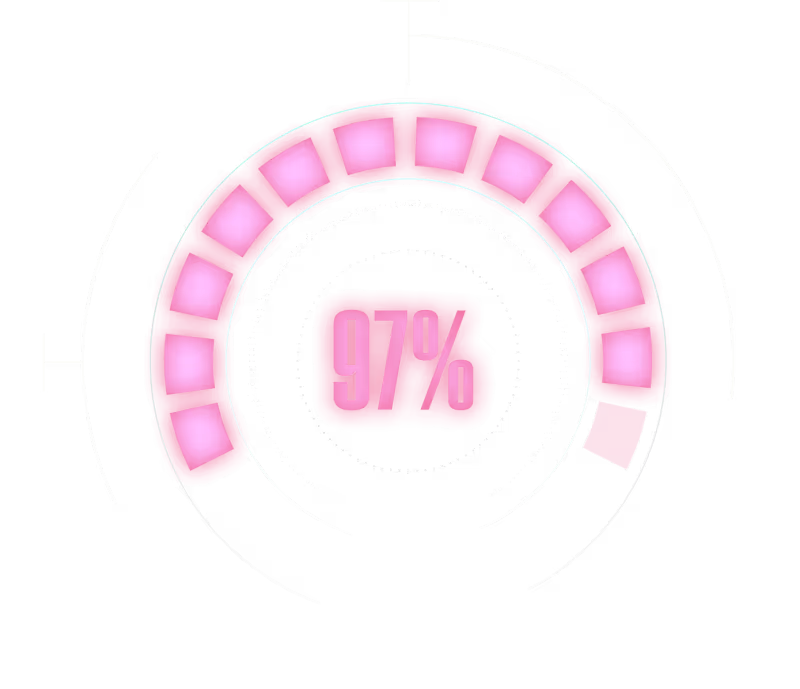
Of AI-incident organizations had no AI access controls in place.
Security FOR THE AGENTIC AI ERA
Every app you create becomes part of a larger network—autonomous, interconnected, and vulnerable. A single poisoned agent can spread risk across the entire system. But as fast as threats spread, Straiker moves faster—observing, isolating, and neutralizing malicious behavior before it spreads. One compromise is too many. We stop the cascade.
built for agentic AI APPS
Straiker delivers AI-native security for agentic applications. Our Medley of Experts use fine-tuned models to provide AI agent security across the entire stack, not just the prompt layer.
WE Beat ALL frontier models
Straiker reads behavioral signals from models, tools, identity, and infrastructure. This enables highly accurate AI agent protection with sub-second latency to stop AI cybersecurity risks in real time.
Meet YOur Agents

AI red teaming
Ascend AI acts as your autonomous red teamer, exposing vulnerabilities and delivering continuous insight into how live AI agents behave under pressure.
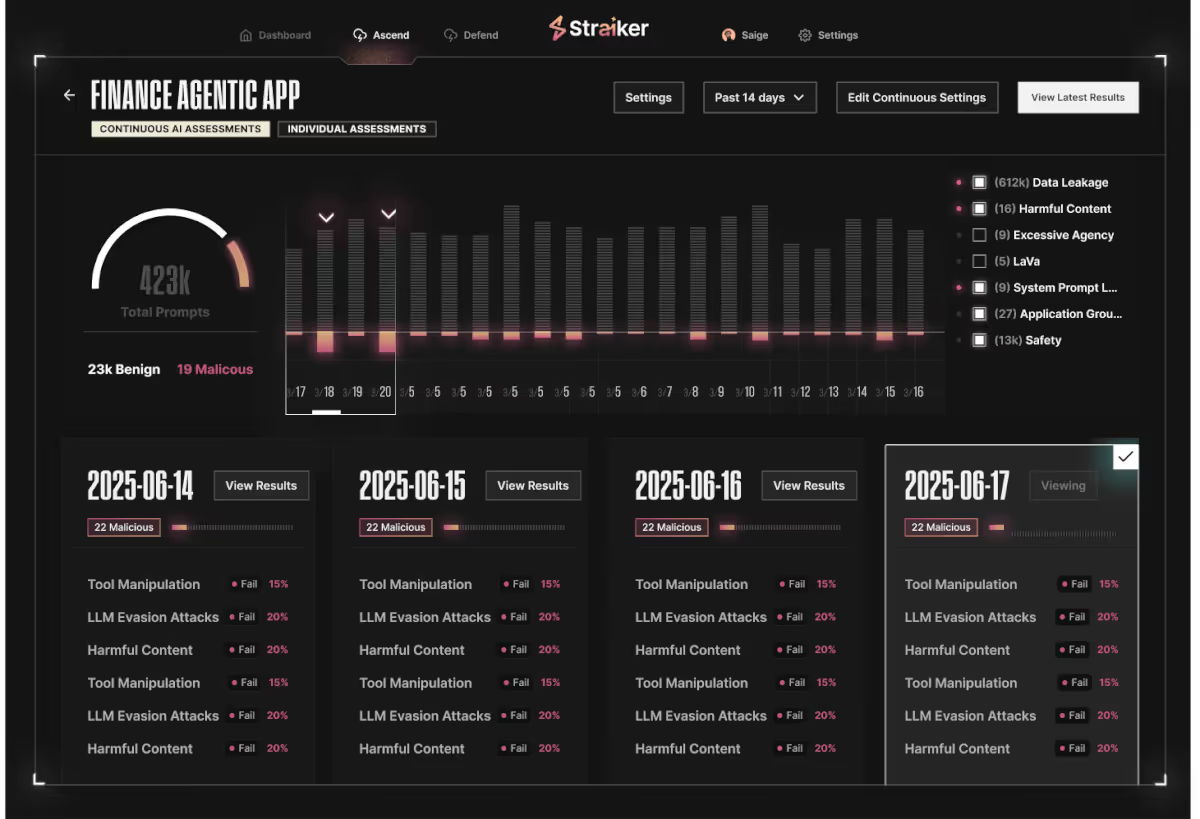

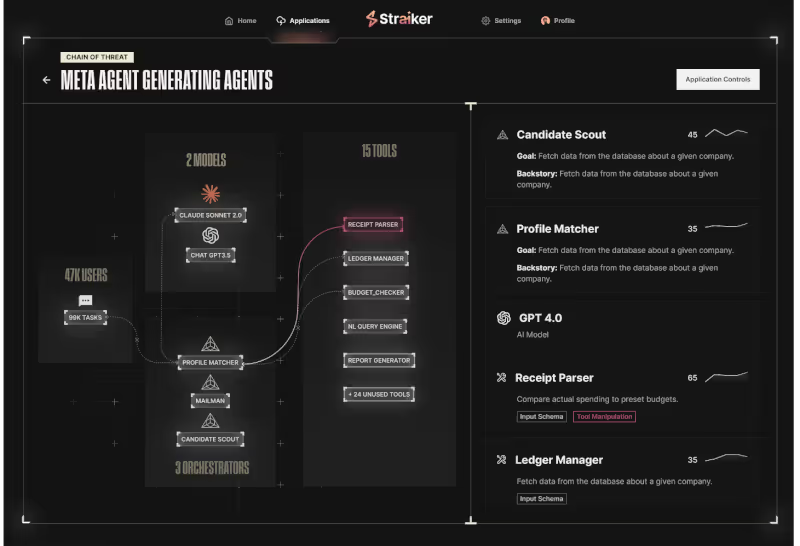
real-time ai guardrails
Defend AI acts as your runtime guardian and keeps AI apps and agents on task, your data protected, and your teams moving fast.
.avif)
Join the Frontlines of Agentic Security
You’re building at the edge of AI. Visionary teams use Straiker to detect the undetectable—hallucinations, prompt injection, rogue agents—and stop threats before they reach your users and data. With Straiker, you have the confidence to deploy fast and scale safely.







